CSaaS: Customizable Cybersecurity Platform and Service Delivery for Enterprises, SMBs, and Governments
CDC-ON® is a SIEM, SOAR, Integrated and Augmented EDR-XDR-MDR. CDC-ON® can save your business up to 50% on SOC delivery costs. Our team brings increased bandwidth and expertise for your specific problems.
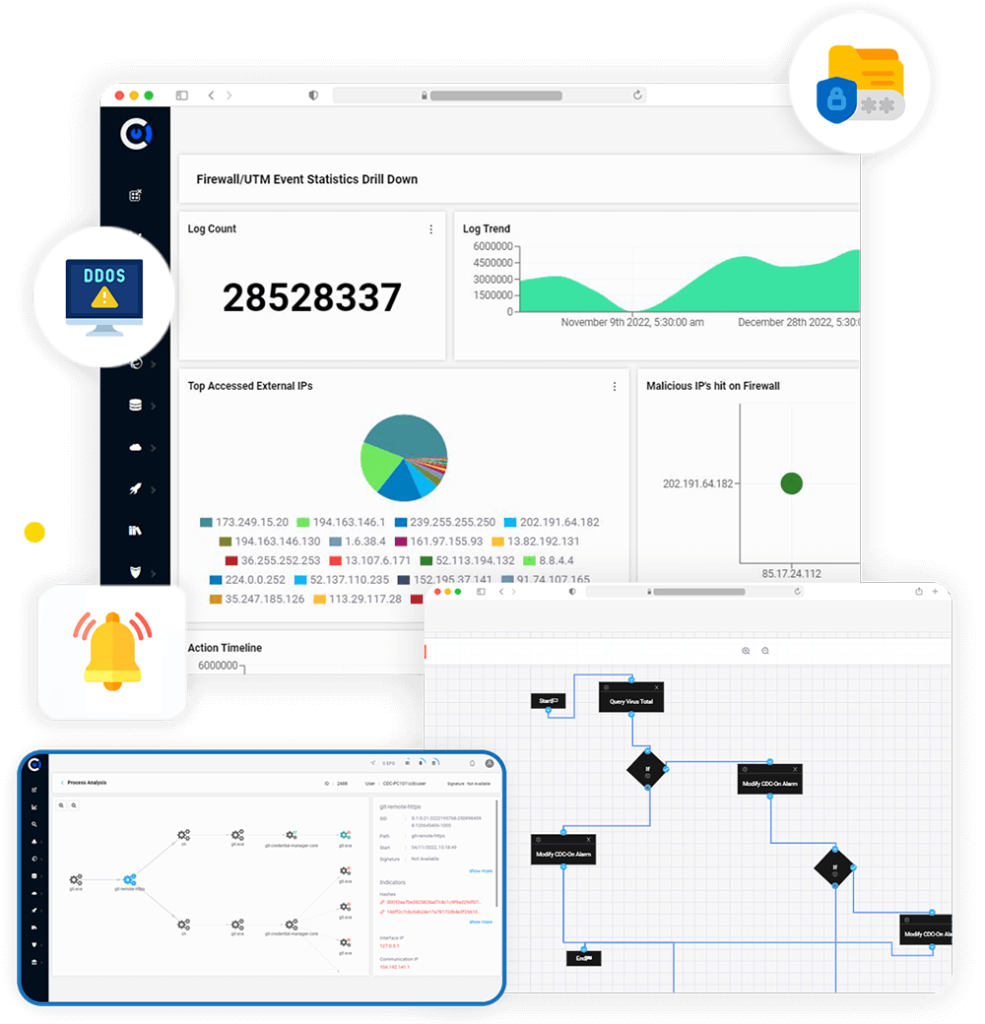
CDC-ON® and services are deployed by several government and critical assets.










What Makes CDC-ON® Different?
We help build or integrate your own unique and niche SOCaaS utilizing CDC-ON® that is customizable at code and API level.


People
We augment your staff with SOC L1/2 analysts. CDC-ON® takes care of the tough hours to allow you to focus on running your business.

Platform
CDC-ON® integrates/replaces any SIEM, EDR, XDR, and provides a full-service SOC platform custom built for your business.

Technology and Process
A comprehensive, scalable cybersecurity solution, tailormade to meet your specific needs. Our platform is 100 percent customizable. Guaranteed.
About Ciber Digita Consultants
Ciber Digita Consultants believes that digital security should be available and affordable to everyone. Through our zero-trust architecture and digital services, CDC stands firm: a rock-solid barrier against threat actors.
The future is digital. At Ciber Digita Consultants, we’re here to secure it for you.
How It Works
Build Your Own Custom Cybersecurity Service
Custom CSaaS Platform for IT, OT & IoT:
- Supports multi-tenancy, multi-location.
- Deployments from 100 to 1,000,000+ endpoints.
- Cloud, on-prem or hybrid.
- CDC-ON® collects massive volumes of data in real-time and detects advanced and persistent threats using innovative machine learning algorithms.
- Assisted triaging workflows promotes dwell-time reduction.
- Inbuilt ticketing and KPI review engine - Ensure strict adherence to SLA.
- Reduced implementation and engineering time.
- Inbuilt compliance auditing and forensic log collection.
- Inbuilt CDC-ON® Agent or clients can choose their own preferred XDR.
- Seamless integration with leading SIEM tools and technologies.
CDC-ON® Base Platform:

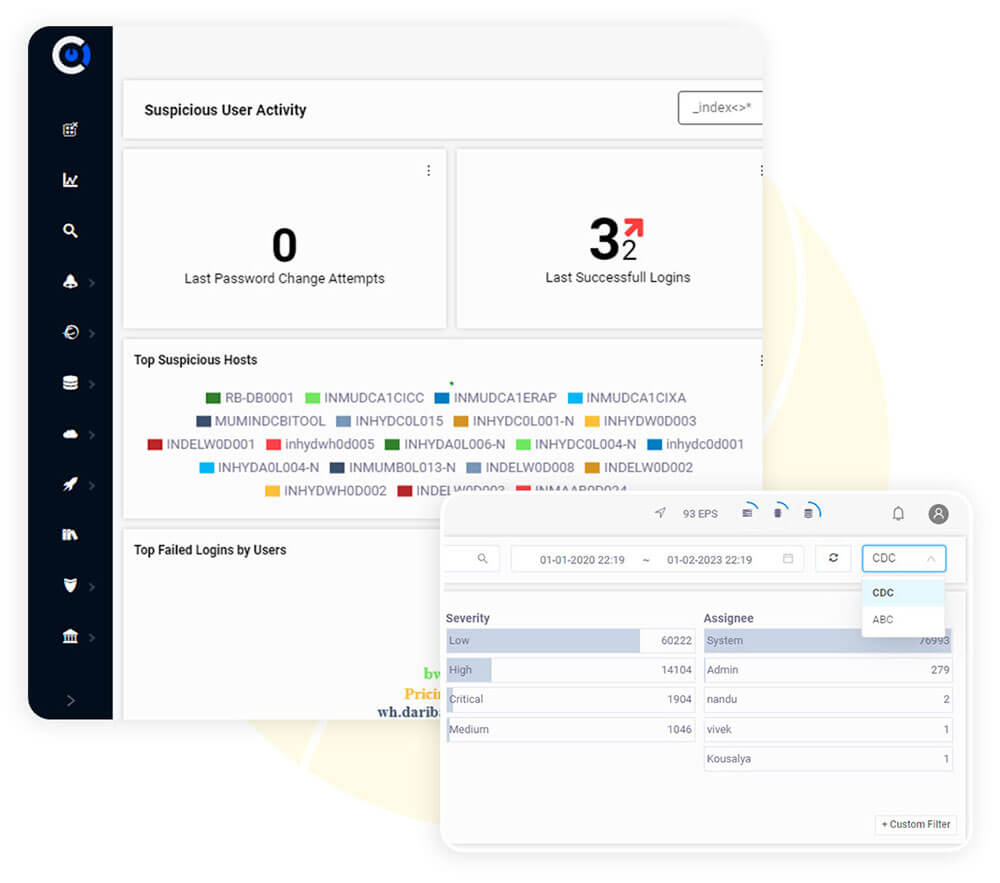
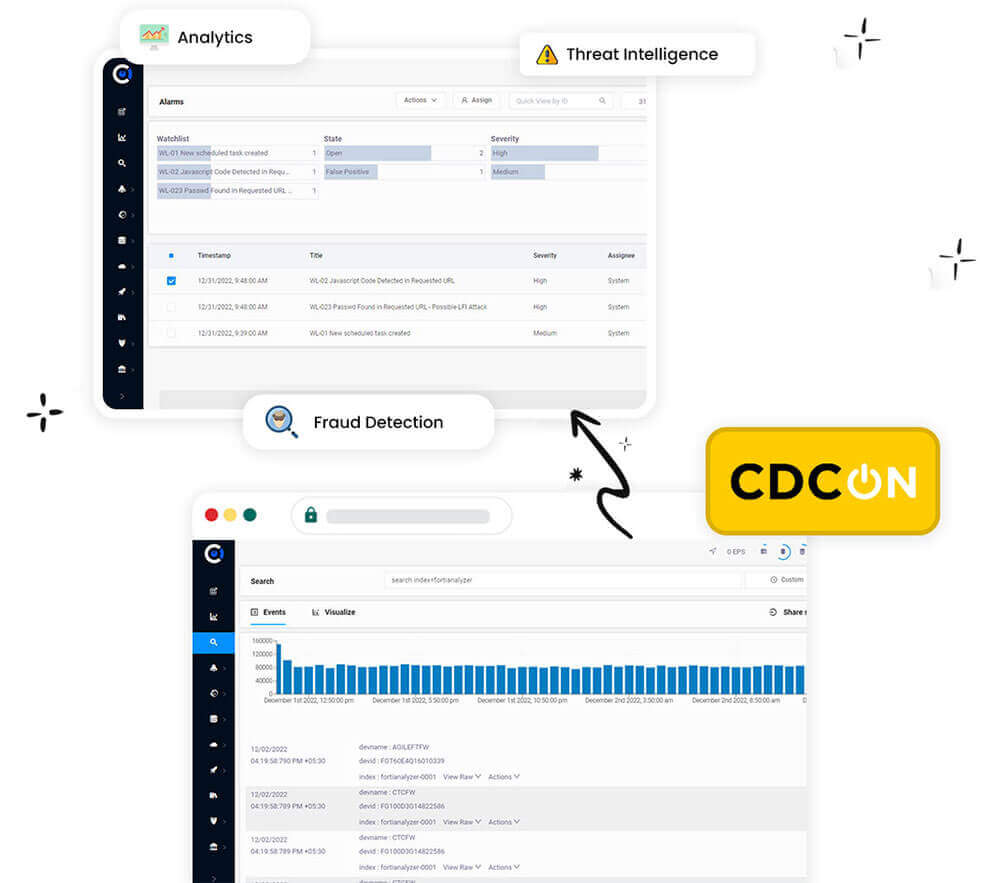
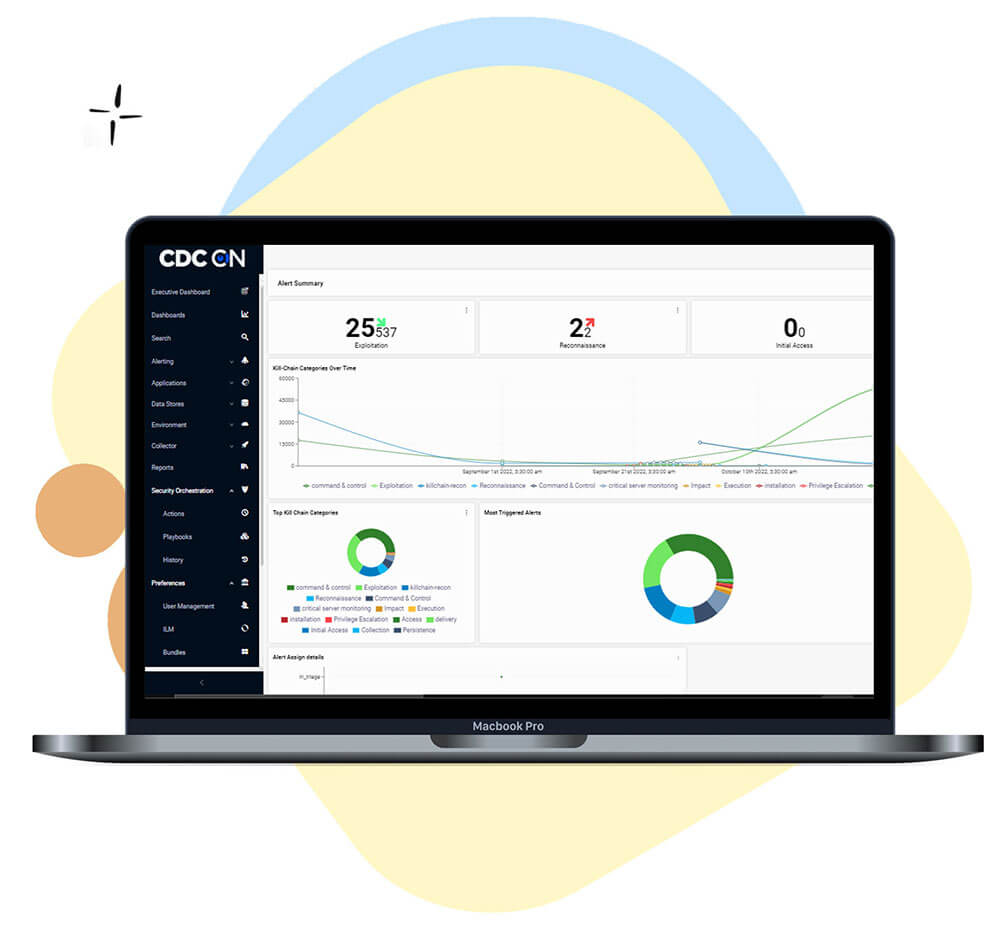
Advanced Visualizations & Dashboards (SIEM)

Alert Remediation Workflow & Advanced Correlation E-mail, Cloud Security

Availability and Performance Monitoring (NOC)

Simple and Powerful Log Searching Capability

Built-in Security Orchestration, Automation & Response: SOAR, Threat Intelligence

Advanced Detection & User Behavior Analytics (UBA)
Testimonials
Our Clients are Happy They Chose CDC-ON®
Ready for a Demo?
Our team can show you how we can:
- Reduce dwell-time of an attack.
- Stay ahead of your threats with increased protection by using customized, effective, integrated CSaaS tailor made to your needs.
CDC-ON® can help save 50% on your SOC deployment and operations.
Get Started with CDC-ON®
Request a 30 minute demonstration.

